WR703N with GPS Module
This tutorial uses the WR703N serial port with a u-blox REYAX RY836AI GNSS receiver module for a super-portable War-Walking / War-Driving device.
Read More
Openwrt for the GL-iNet (v 2) – Bypass 802.1x Port Security

Bypass 802.1x Port Security w/ Openwrt
Background
During an internal and wireless penetration I was unprepared for the port security in the environment. I had to travel internationally and the Statement of Work and Rules of Engagement did not detail the extent of the internal testing and what was to be tested. Penetration Testers know what it is like to conduct a “Penetration Test” when sales staff and client management setup the engagement. Needless to say I was upset at the delay only due to the time it would take to configure a device to bypass the port security when I only had a week onsite to conduct the testing. Luckily I had brought along my PCEngines Alix 62f (used previously in my Custom Power Pwn). I had brought it for the wireless testing as it was configured for wireless client attacks. Using the work done by Alva Lease ‘Skip’ Duckwall IV and presented at DEFCON 19 in 2011. I reconfigured the Alix to show the client how easy it is to bypass port security. Well I never want to encounter a similar situation again but I also don’t want to carry yet another device with me when traveling. Having the device be as small as possible while service multiple purposes would be ideal. That is why I’m using the GL-iNet with the Openwrt operating system for this project.
Version 2 of this tutorial builds off of version 1 but additional work is done to help you build an image that will allow you to bypass 802.1x port security without any post install customization (as shown in this previous post). Also some network recon tools are included as well.
Read More
Your Physical Security Toolkit – The GL-iNet
 In 2013 I presented at the Rhode Island Bsides about the work I did with the TP-Link wr703n creating a “Super” Minipwner (real ingenious name). Below is the abstract for my talk.
In 2013 I presented at the Rhode Island Bsides about the work I did with the TP-Link wr703n creating a “Super” Minipwner (real ingenious name). Below is the abstract for my talk.
The TP-Link WR703N is a low cost wireless access point that has replaced the venerable Linksys WRT54G as the most popular device to crack open and tinker with. Many project tutorials have sprung up on how to hack this device from a hardware and software perspective. One such project is the “minipwner” coined by Kevin Bong with his site www.minipwner.com. This talk builds off of that concept by trying to upgrade and implement as many features as possible while still keeping the original case. Why the original case? Because I said so. We double the RAM and flash storage, add a usb hub, usb sdcard reader storage, usb to Ethernet port, serial port over usb, and finally we have integration with the Teensy so you can run keyboard commands remotely over WiFi. I call this device the very original name of super-minipwner.
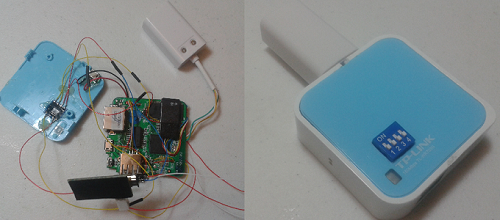
The TP-Link wr703n is a fun device to tinker with but I want to step it up a notch and use a device that already had two network ports. I always pined after the wr720n (the Chinese model) and even got my hands on one to play with. However, the RAM and Flash were the same as the wr703n and I didn’t want to ruin the device upgrading it. 4mb of flash storage and 32mb of RAM just isn’t going to cut it. Also the devices are harder to find and more expensive…and nobody is selling services on Ebay to upgrade the wr720n like the wr703n. Though if you asked him I bet he would. The router is also larger in size due to AC outlet plug.
Then the Openwrt forums started discussing the GL-iNet. I was hooked the moment I saw it. They took the wr703n and added everything a hacker could want. Two network ports, easy access to GPIO and Serial pins, 64mb of RAM, 16mb of flash, internal power header, and a connector for an external antenna. This all in the same dimensions of the wr703n. The new penetration testing device created using the GL-iNet will be documented in several parts.
Part 1 – Building Openwrt for the GL-iNet
Part 2 – Using Openwrt to Bypass 802.1x Port Security
Part 3 – Remote HID Attacks with a Teensy 2.0 – The Build
Part 3.1 – Remote HID Attacks with a Teensy 3.1 – The Build
Part 4 – Remote HID Attacks with a Teensy – Testing Your Build / Getting Started
Part 5 – Remote HID Attacks with a Teensy – Peensy Code
Recycle WR703N Case for the Expander
 The TP-Link WR703N Expander is an open source hardware extension to the TP-Link WR703N. It was created by Kean Electronics (http://www.kean.com.au/) and can be purchased from Seeed Studio (http://www.seeedstudio.com/). I won’t go into the details of what the Expander includes and what you can do with it. This article details how I created my own enclosure for the Expander since I don’t have a 3D printer and I didn’t want to purchase the enclosure from one of the 3D printer fabrication sites.
The TP-Link WR703N Expander is an open source hardware extension to the TP-Link WR703N. It was created by Kean Electronics (http://www.kean.com.au/) and can be purchased from Seeed Studio (http://www.seeedstudio.com/). I won’t go into the details of what the Expander includes and what you can do with it. This article details how I created my own enclosure for the Expander since I don’t have a 3D printer and I didn’t want to purchase the enclosure from one of the 3D printer fabrication sites.
Ubuntu 14.04 – JtR 1.7.9 Jumbo 7 – oclHashcat 1.2 – NVIDIA CUDA
This tutorial does the least amount of compiling using as much as possible from the Ubuntu 14.04 repositories.
Read More
John the Ripper 1.7.9 Jumbo 7 with Nvidia CUDA GPU Support
Install the latest John the Ripper 1.7.9 with the Jumbo 7 patch. Before downloading John you will need to install the CUDA development files. See this blog article for instructions on how to install the latest Nvida drivers for Ubuntu 13.10 and latest CUDA development files.
Read More
Install or Update CUDA to the latest version (5.5)
We are going to install / update CUDA to the latest version (5.5). For this tutorial we will be running Ubuntu 13.10 and install the latest Nvidia driver from a repository. We will not have the CUDA installation install the drivers.
Password Pwn Stew – Ettercap, Metasploit, Rcrack, HashCat, and Your Mom
You can probably get by with leaving off that last part of the title and still succeed with this attack. Today we will be making a Password Pwn Stew. Add a little Ettercap (link), with a dash of Metasploit (link), a smidgen of password cracking with Rcrack (link) and Rainbowtables (link), and if required a pinch of Hashcat (link) to taste. You will have yourself some tasty pwnage.
Note, your mileage may vary with this stew. I’m not Martha Stewart. Also the stew analogy ends here 🙂
Read More
oclHashcat, HalfLM (netlm), and Bruteforcing the Second Half
When you obtain a NetLM password hash with the known challenge of 1122334455667788 you are able to utilize the HALFLMCHALL rainbowtable to identify the first seven (7) characters of the password. The second half is left to identify. Tutorials exist (including my site, as well as here and here) on how to capture the NetLM hash using Metasploit. Metasploit comes with a Ruby script in the tools folder that will bruteforce the remaining characters of the password when you provide the complete NetLM hash and the first seven (7) characters of the recovered password. However, for passwords that are 11+ characters it is time prohibitive to bruteforce the remaining characters as show below.
Read More
Compiling and Installing Ettercap v0.8.0 and Latest Source
The latest version of Kali Linux comes with the most current version of Ettercap. But some people are gluttons for punishment and still like to compile stuff themselves so see below.